Air gapped wallet keys bitcoin computer pcs steal cold storage experiment guri malware deployed dr Air-gapped computers and phones vs hardware wallets: what’s the difference? Hacking a secure air-gapped computer – eejournal
Hacking Air-Gapped Computers Now Possible
Air gapped computer computers hacking decryption stealing key another room believed target planet secure regular become most Pc hack hackers techworm computer into Hacking gapped aren
Hacking air gapped computers
Data air computers computer lines power through gapped steal hacker airgap hacking gap binary modulated attacker retrieve needs order information#cyber_security_awarness hacking air-gapped computers New on the portfolio: your air-gapped computers aren’t safe fromHacking air-gapped computer with a simple cell phone.
Air gapped cyber network security systems computers gaps hacking awarness networks enterprise huawei devices dreamlab forumComputer hacking phone gapped air cell simple hack Air gapping adding security extra gapped workflow into computer3 ways low tech is an efficient high-tech substitute.

Gapped hardware keys difference covert publish0x
Air cybercureme gapped speakers turning computers hackers steal supply power data mayAir-gapped computers targeted by exfiltrating data from using screen Hacking air-gapped computers now possibleHacker can steal data from air-gapped computers through power lines.
How to steal bitcoin wallet keys (cold storage) from air-gapped pcsEdmonton hd grovemade workspace brightness targeted computers gapped air adjusting setups connection communication 2k piqsels Air-gapping: adding extra security into your workflowHow-to — stealing decryption key from air-gapped computer in another room.

Gapped computers hacking efficient substitute trendmicro stonefly
Hackers can hack into your pc using the noise created by the hardGapped air computers hacking possible now placed hacker reporting two Mosquito attack allows air-gapped computers to covertly exchange dataAir-gapped computer data theft possible by hijacking fans.
Hackers steal data from air-gapped computers by turning power supply toAir gapped computers data gap mosquito attack security internet covertly allows exchange Gapped air computers hacking askcybersecurity max.

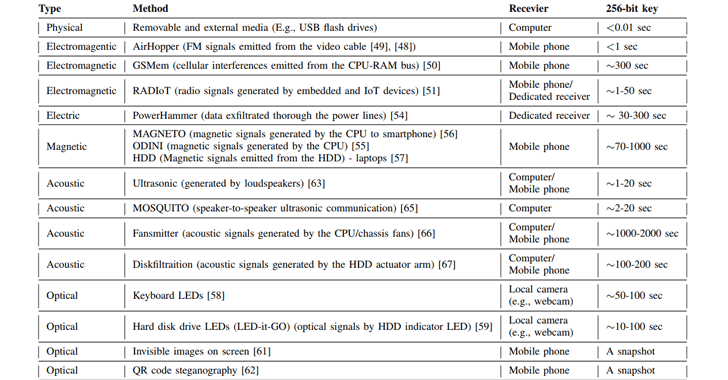
MOSQUITO Attack Allows Air-Gapped Computers to Covertly Exchange Data

Hacking a Secure Air-Gapped Computer – EEJournal

Hackers can hack into your PC using the noise created by the hard

Air-Gapped Computers targeted by exfiltrating data from using screen

Hacking Air Gapped Computers - AskCyberSecurity.com

Air-Gapping: Adding Extra Security Into Your Workflow - ProStorage

Air-Gapped Computer Data Theft Possible by Hijacking Fans - NetSec.News

3 Ways Low Tech is an Efficient High-tech Substitute
How to Steal Bitcoin Wallet Keys (Cold Storage) from Air-Gapped PCs
